Keeping your
memory safe
Your privacy is foundational to everything we build. Unlike typical AI applications, we designed a system where your data is encrypted by default and decrypted only inside a hardware-isolated enclave for the moment it's needed, meaning not even Pickle can see them.

Today’s AI industry abandons data encryption for the sake of convenience. We reject that. Instead, we offer a new architecture as the standard.
security architecture
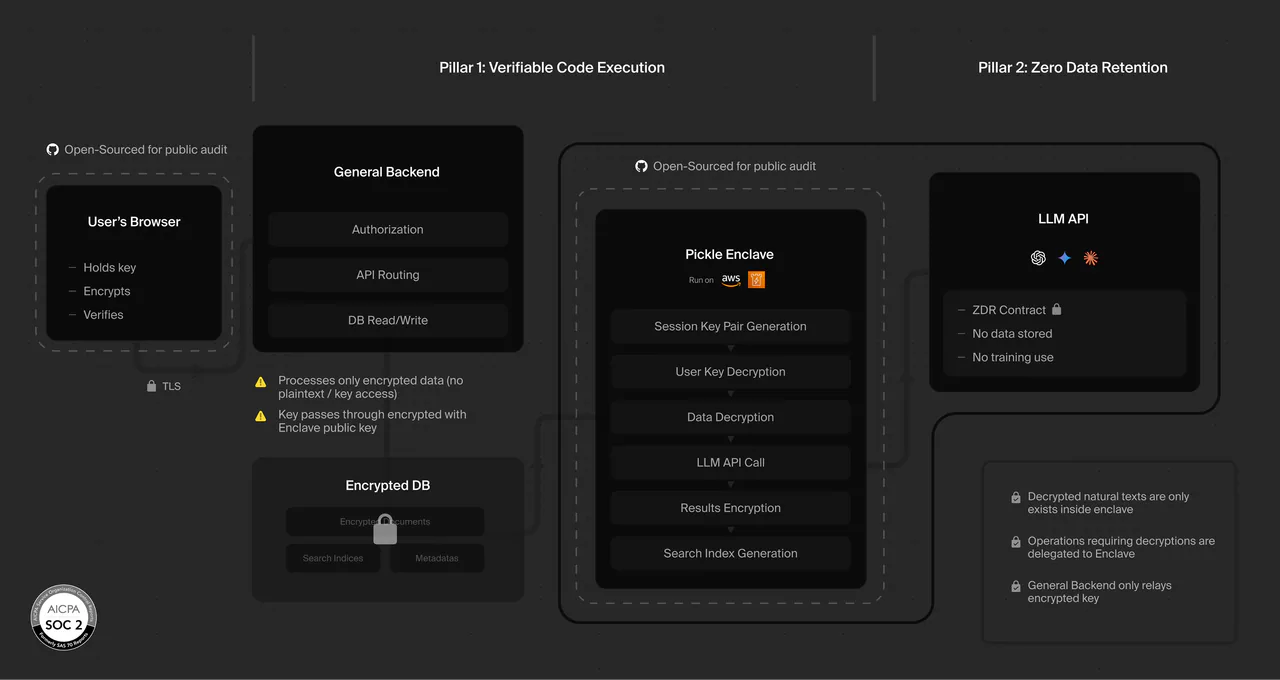
Pickle Enclave for Pickle OS
No one can read your data. Even us.

Pickle Enclave is a secure, isolated environment designed to safely decrypt and process your data. It is controlled exclusively by the key on your device and vanishes the moment the task is complete, ensuring your Memories remain secure.
You control your encryption keys
Your data is encrypted on your device before it is sent to us. Only you have the encryption keys. We do not store, manage, or have access to your keys at any time. That means we cannot read your data, even if we wanted to. Your data can only be decrypted temporarily, inside the secure environment, to perform the task you requested.
Data exists only while it's needed
When your data is decrypted, it exists only in memory and only for a short time. It is never written to disk or saved anywhere in readable form. As soon as the task is finished, the memory is cleared. Nothing readable is kept, logged, or reused later.
The system can verify itself
The secure environment verifies that it is running the correct, approved software before it starts. If the software were changed in any way, the system would detect it and stop running. This ensures your data is processed only under the expected and approved conditions.
See how Pickle 1 keeps
everything private.

Keep your view private. The AR display is designed to reflect light only towards the user, making its contents invisible from the outside. See freely, even in a crowd.

Lock with your fingerprint. Pickle 1 can be unlocked only with your fingerprint. Your personal intelligence exists exclusively for you.
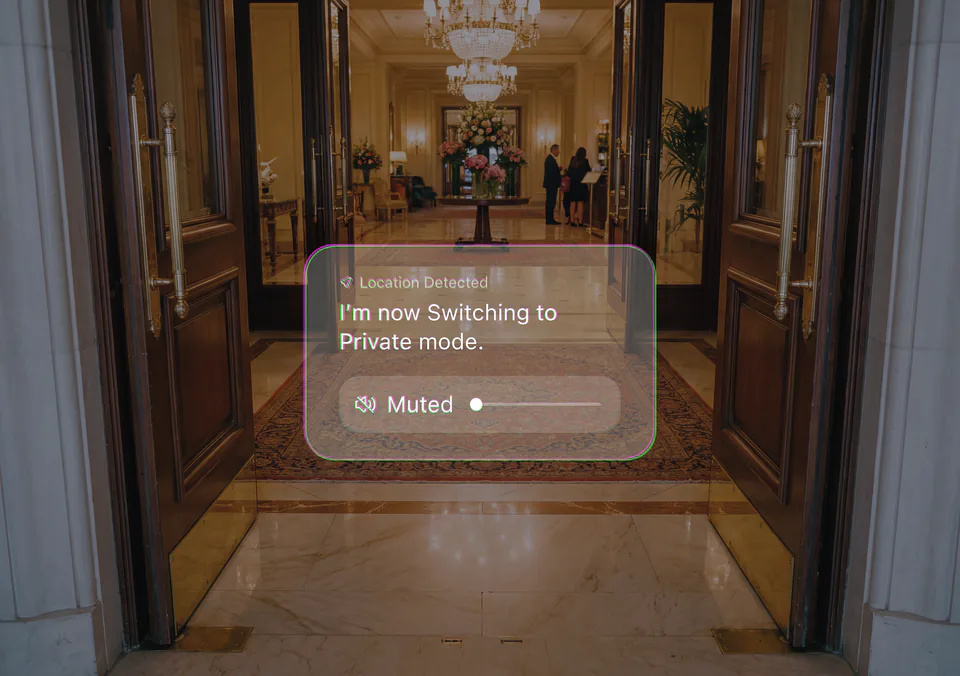
Choose where it speaks to you. You can set Pickle 1 to speak to you directly only in locations you desire. It ensures your private conversations remain private.
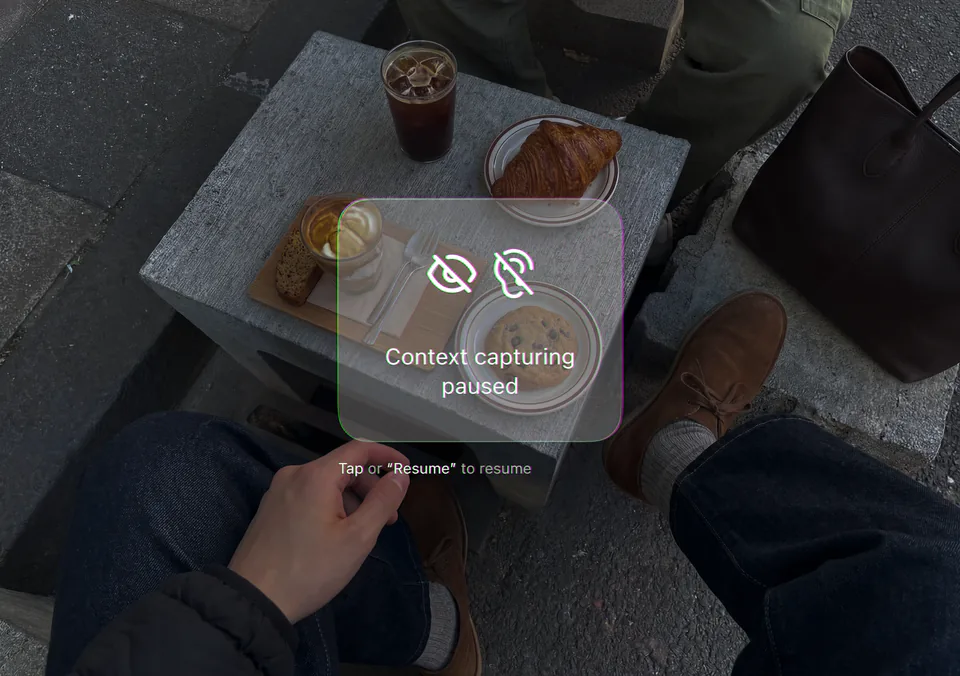
Go off the record instantly. Stop capturing your context at any moment via voice commands, gestures, or a simple touch. You can also immediately discard any memories to ensure nothing remains.
Discover our additional layers
of privacy & security.
Define your context
capture boundaries
You have granular control over what system captures. Toggle specific contexts to curate your memory stream exactly how you want it.
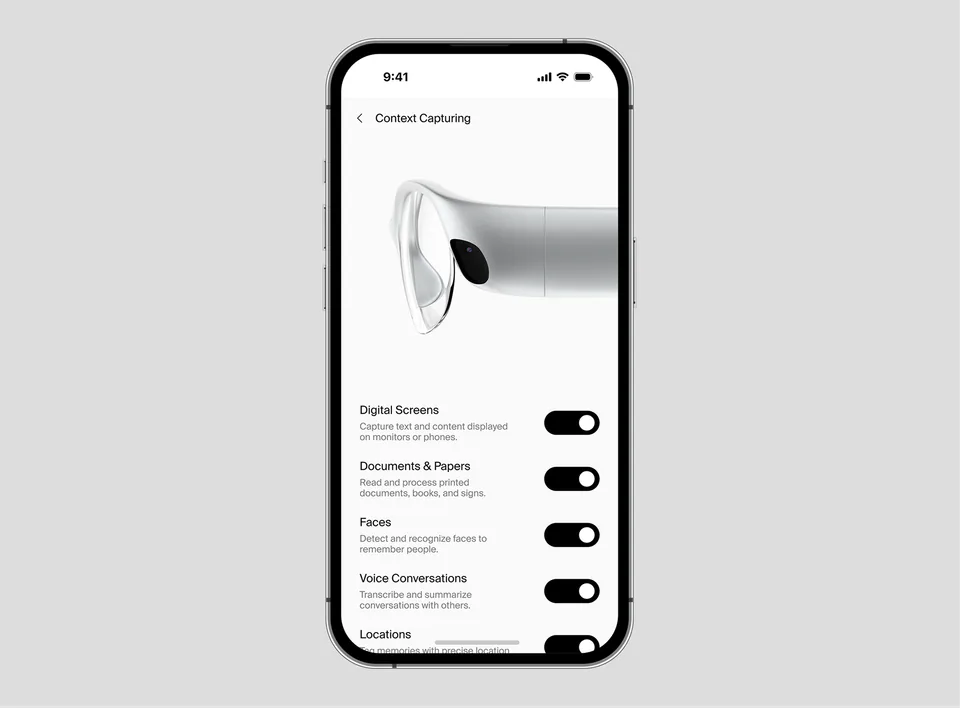
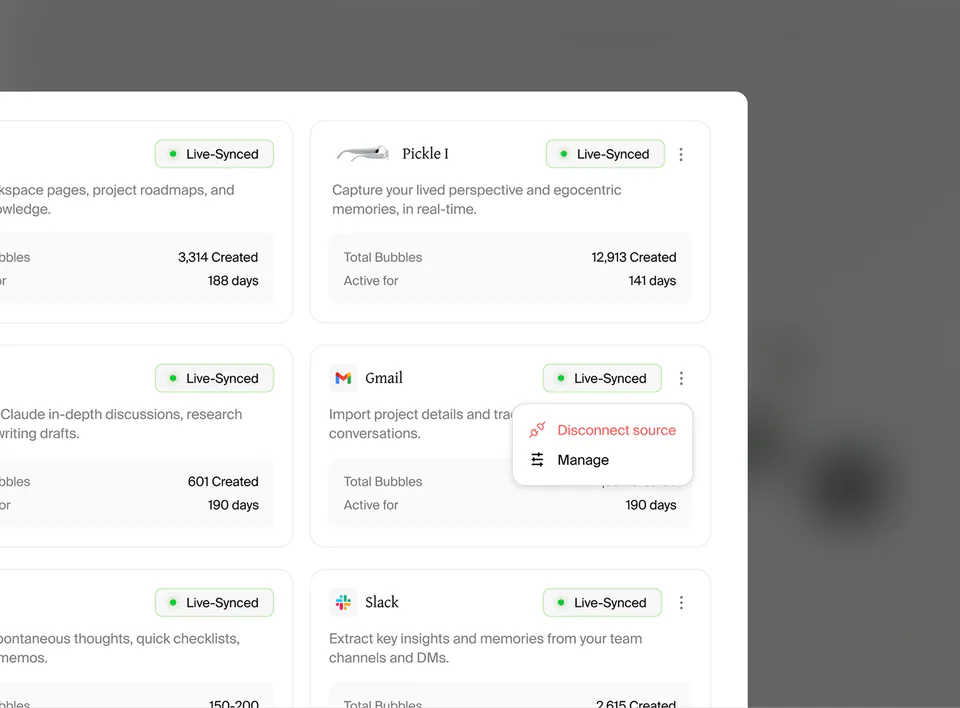
Take full control
of your data
Disconnect sync sources from Pickle OS instantly or permanently delete your account and all memories with a single click.
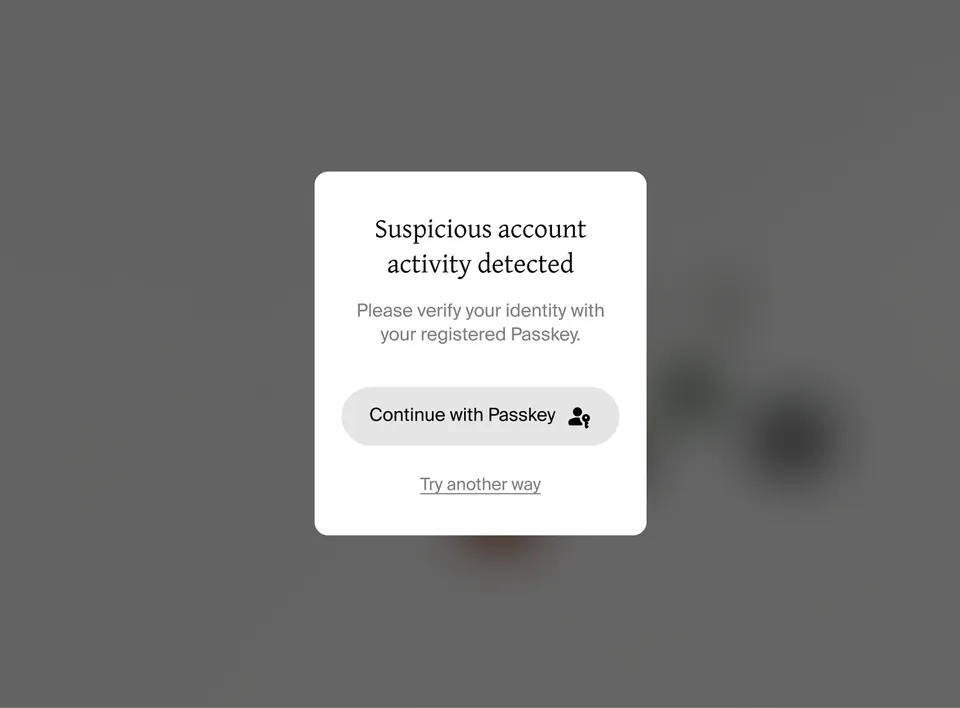
Protects
your account
Multi-Factor Authentication (MFA) and real-time anomaly detection actively block unauthorized access, ensuring that no one but you can touch your data.
Frequently Asked Questions
Pickle Enclave is a hardware-isolated execution environment built on AWS Nitro Enclaves. Think of it as a digital vault where your data is processed. Unlike standard servers, the Enclave is completely isolated from the rest of our infrastructure—meaning no one, including Pickle’s own developers, root administrators, or cloud providers, can access its memory or storage. It is the only place where your data is ever decrypted, and it is programmed to wipe all sensitive information from its memory immediately after processing your request.
No. We have designed our architecture so that we structurally cannot see your data, even if we wanted to. Your original data is encrypted using a Master Key (user_secret) that lives exclusively in your Browser Extension. When you use Pickle, this key is sent directly to the secure Enclave using ephemeral encryption, bypassing our general backend entirely. Our database stores only encrypted text (ciphertext) which looks like random garbage without your key. Since we do not possess your key and cannot access the Enclave's memory, decryption by our team is mathematically impossible.
No. We strictly limit data exposure to the LLM providers (like OpenAI or Anthropic) required to answer your questions, and this is protected by two major safeguards. First, we operate under Zero Data Retention (ZDR) contracts, which legally bind these providers to never store your data or use it to train their AI models. Second, the connection to these providers uses TLS encryption that terminates inside the Pickle Enclave. This means our servers act only as a "blind relay"—we pass the encrypted signal along, but we never see the plaintext content being sent to or received from the AI.
You don't need to trust our word; you can verify the code yourself. Pickle operates on a "Verifiable Privacy" model:
- Open Source: Our Enclave and Extension code is open-sourced for public audit.
- Cryptographic Proof: Before your browser sends any keys, it performs a "Remote Attestation." It checks a cryptographic signature from AWS to prove that the code running on our server is identical to the safe, open-source code you see on GitHub. If the code on the server has been tampered with, your browser will reject the connection immediately.
Defining the privacy & security standards
for the soul computing era
Pickle, Inc. ("Pickle," "we," "us," or "our") builds a personal memory system that allows individuals to securely store, process, and grow their own data context. This policy explains how we collect, use, and protect your information when you use our websites, browser extensions, and connected devices (collectively, the "Services").
Our Core Security Philosophy
Pickle's mission is to help you preserve your experiences and context — privately and securely.
Our core principles are:
- You own your memories: You control your data, how it's used, and when it's deleted.
- Zero Data Retention for AI: We never use your personal data to train large language models.
- Verifiable Privacy: Data is only decrypted for extremely short periods inside hardware-isolated Enclaves for verified, purpose-specific processing.
- Forward Secrecy: We do not store the keys to your past data. Once a session ends, the keys are destroyed, making retroactive decryption impossible.
- No Selling: We do not sell your data.
Information We Collect
We collect data only to provide and improve the Pickle experience. It is crucial to distinguish between data you own (which we cannot see) and data we process.
Personal Memory Data (Encrypted & Private)
You can upload or connect various forms of personal data to your memory bank. This data remains encrypted at rest and is accessible only through your verified account.
- Content Data: Text, notes, emails (via Gmail), and documents (via Notion).
- Context Data: Calendar events, transcripts, and creative work logs.
- Search Metadata (Blind Indexing): To allow searching without decrypting your data, we store hashed search tokens. Since hash values cannot be reversed, the search index itself exposes no meaningful information to us.
- Vector Embeddings (Orthogonal Transformation): AI search requires vector embeddings. To protect these, we apply a per-user secret orthogonal transformation inside the Enclave. This preserves the mathematical relationships needed for search while hiding the original semantic meaning from our servers.
- Users Key: Your master key, which is generated on your device and never stored in plaintext on our servers.
Privacy Guarantee:
The plaintext of this data exists only in two places:
- Your Client Device (Browser Extension/App).
- Our Secure Enclave (during active processing only). Pickle administrators and databases see only encrypted "garbage" data.
Temporary Sensor & Device Data
When using a Pickle-certified product (e.g., Pickle 1, Glass, camera, or microphone):
- Raw Input: Temporary inputs such as images, videos, voice, or text are briefly processed to extract semantic meaning.
- Immediate Deletion: Original raw data (photos, videos, audio) are deleted immediately after processing.
- Derived Memories: Only the derived, text-based representations ("reprocessed natural-language memories") are securely stored on the server in encrypted form.
Account & Profile Information
We collect basic information necessary to manage your account:
- Name, email, and password (or authentication method).
- Settings and preferences related to your Pickle devices.
- Payment information (processed by third-party secure payment providers).
Optional Analytics (Opt-In)
To help improve Pickle, you may opt in to share de-identified analytics.
If enabled, we collect:
- General usage metrics (login frequency, feature usage)
- Non-identifiable event logs.
We never collect your original text, photos, voice, or memory content for analytics.
Technical Architecture & Security
Our "Privacy by Design" approach relies on a Verifiable Privacy Architecture.
We utilize AWS Nitro Enclaves to process your data.
- Isolation: Code and data inside the Enclave are inaccessible from the outside. Neither the server OS, system administrators, nor anyone with physical access can see inside.
- Remote Attestation: The Enclave cryptographically proves exactly what code is running. You can verify this hash against our open-source code on GitHub.
- TLS Termination: All encrypted traffic from your device and to external AI providers terminates inside the Enclave. Our general servers act as "blind relays" (L4 proxies) that pass encrypted bytes without ever having the keys to read them.
We employ a split-key architecture using HKDF (HMAC-based Key Derivation Function):
- Client Side (user_secret): Generated by your device. Stored in extension-only storage. Never sent to the server in plaintext.
- Server Side (Ephemeral Keys): Unlike traditional systems that store a "Root Secret," our Enclaves generate random Ephemeral Keys (SK_eph) at boot. These keys exist only in the Enclave's volatile memory (RAM).
- The Handshake: Your device only sends your key after verifying the Enclave's attestation. It sends the key encrypted with the Enclave's public key. The General Backend relays this ciphertext but structurally cannot decrypt it.
- Forward Secrecy: When an Enclave shuts down or restarts, these keys are permanently destroyed. This means that even if a bad actor seized our servers later, they could not decrypt past logs or data because the keys no longer exist.
How We Use Your Data
We use your data only to provide and improve your personal Pickle experience:
- To sync, organize, and retrieve your stored memories
- To personalize responses or recommendations from your memory bank
- To operate connected devices and software
- To maintain secure account access and provide technical support
- To generate derived representations (semantic embeddings, summaries, or hypotheses) strictly within your encrypted context
Your data is never used for advertising or model training.
Processing occurs only under encryption, and decrypted access is limited to short, auditable sessions within verified systems.
Data Sharing & Zero Data Retention (LLMs)
Pickle does not sell or share user data with advertisers. We share information only when necessary to operate our Services, under strict constraints.
To provide intelligence, we must send data to Large Language Model providers (e.g., OpenAI, Anthropic). We strictly enforce Zero Data Retention (ZDR) contracts:
- No Training: Your data is never used to train or fine-tune their models.
- No Retention: Data sent via API is discarded immediately after the response is generated.
- Direct Routing (TLS & Blind Relays): We call API endpoints directly from inside the Enclave using TLS. Our architecture ensures that our own non-Enclave servers act only as blind relays and cannot log the plaintext of these requests. You can verify this in our open-source code, which ensures that neither we nor the cloud provider can intercept the traffic.
We work with trusted providers for:
- Hosting: AWS (Encrypted blobs only).
- Payments: Stripe/LemonSqueezy (Financial data only).
- Security: Fraud prevention partners (Metadata only).
Data Retention & Deletion
We retain user data only as long as necessary to provide services or as required by law.
- Raw Sensor Data: Deleted immediately after processing.
- Encrypted Memory Data: Retained until you delete it or close your account.
- Your Right to Delete: You can delete your data at any time via account settings or by emailing contact@pickle.com.
- Deletion Mechanism: Upon deletion, all user-identifiable data and derived representations are erased. Backups are purged within 30 days. Because we do not hold your master keys, deleting the encrypted data renders it mathematically irretrievable immediately.
Threat Model & Limitations
What We Defend Against:
- Service Operator Snooping: We cannot see your data (Enclave isolation).
- Database Hacks: Attackers only get encrypted "garbage."
- Retroactive Decryption: Past data remains safe even if keys are compromised later (Forward Secrecy).
Limitations:
- Key Loss: Because we do not store your master key, if you lose your key/extension and have no backup, we cannot recover your data.
- LLM Provider Breach: If an LLM provider violates our ZDR contract, we cannot technologically prevent that (though they are legally bound not to).
User Rights
You have full control over your data. You can:
- Access and export your memories.
- Correct inaccurate data.
- Revoke third-party integrations.
- Request full account deletion.
- Manage analytics and consent preferences.
To exercise your rights, email us at contact@pickle.com or use your in-app privacy dashboard.
Children's Privacy
Pickle's Services are intended for individuals 18 years and older. We do not knowingly collect personal data from minors. If you believe a child's data was submitted in error, contact us at contact@pickle.com for prompt deletion.
International Data Transfers
Pickle is headquartered in the United States. If you access our Services from outside the U.S., your information may be transferred to servers located in the U.S. or other jurisdictions. We follow standard contractual clauses and best practices to ensure adequate protection of your data.
Changes To This Policy
Additional Commitments
- Zero-Knowledge Storage: Pickle systems cannot read user content without your authenticated session.
- No LLM Training: Your personal data is never used to train or fine-tune any large language model.
- Data Minimization: We only process what's necessary, and discard raw inputs immediately after use.
- Transparency Dashboard: All data events (uploads, access, deletions) are visible to you within your account.
- Ethical Safeguards: Pickle adheres to the highest standards of digital dignity, transparency, and autonomy.
- Open Source Verification and Reproducible Builds: It is not enough to be open source. We support reproducible builds, allowing you to verify that the extension installed on your browser and the binary running in our Enclave matches the published code on GitHub exactly, byte-for-byte.
Contact Information
Pickle, Inc.
Email: contact@pickle.com
Address: 5 Pear Ct, Hillsborough, CA, 94010